I recently needed to debug some D365 x++ code, and while debugging I was running into code from a 3rd party ISV that I was unable to see. I needed to be able to view the logic running to replicate certain pieces in other custom development.
To get past this hurdle, I downloaded ILSpy, this allowed me to drag and drop the dll files and the netmodule files into the ILSpy UI and see the underlying code. Not all of it was truly x++ code, but the logic was still clearly readable and was quickly decipherable to the corresponding x++ code.
https://github.com/icsharpcode/ILSpy/releases/tag/v7.2.1
The above link is for 7.2.1 which is the current stable version. Look for the most updated stable release for future downloads.
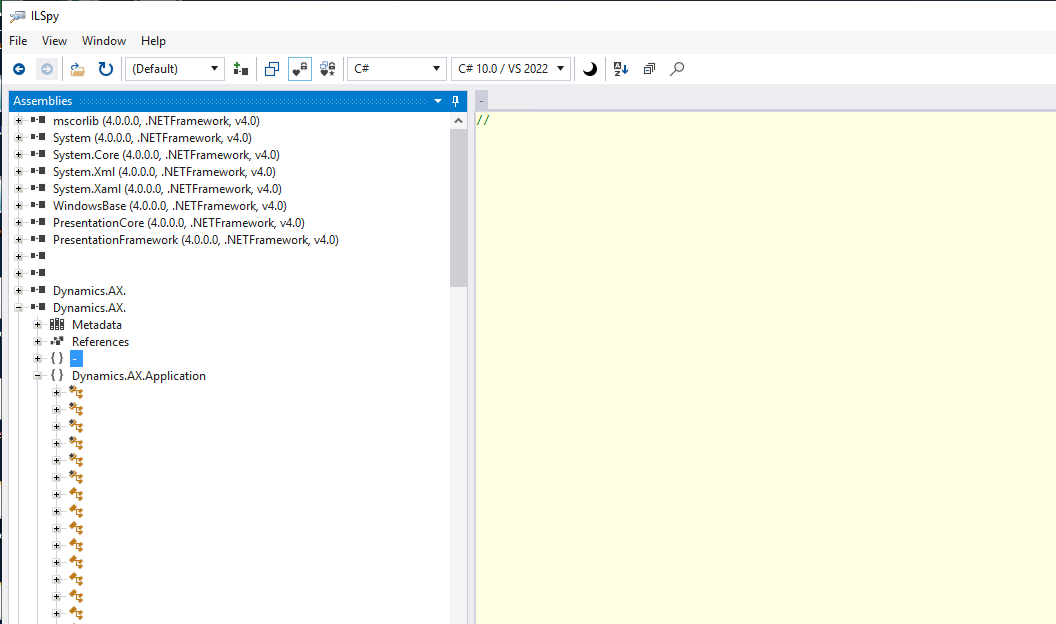
To use ILSPY, download the zip file from the above link. Unzip the file and run the executable. This will lauch the UI seen pictured below. Here you can drag and drop the dll/netmodule files provided by the 3rd party ISV in question. Then you can click through the tree structure on the left and select a class to view in the window on the right. The output code is not x++ code but can be easily read and transformed into the corresponding underlying code.
Keep reading about D365 tips and tricks here: https://markedcode.com/index.php/category/d365/
For technical questions, please visit https://d365techsupport.com



